The Pentagon Just Flipped the Switch --> CMMC Compliance Is Now Live!
Jim Leone
11/11/20253 min read
The Moment We’ve Been Waiting (and Waiting) For ...
After years of delays, revisions, and rumors, the Pentagon has finally thrown the switch, as of November 10, 2025, Cybersecurity Maturity Model Certification (CMMC) is officially being enforced for new Department of Defense (DoD) contracts.
That’s right, the world’s largest defense contractor ecosystem, thousands of suppliers, vendors, and service providers, now must prove they can protect sensitive government data or risk being benched from future contracts.
For anyone working with the DoD, it’s no longer a “someday” conversation. It’s showtime.
So, What Is CMMC?
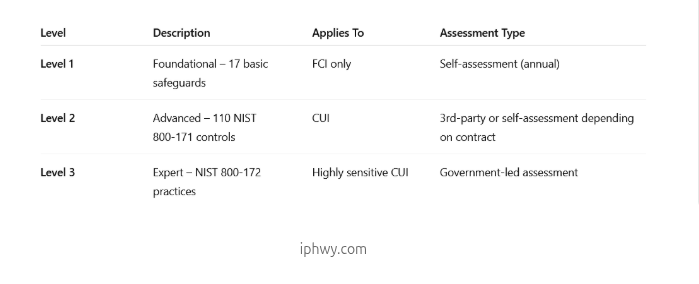
CMMC (Cybersecurity Maturity Model Certification) is the DoD’s unified cybersecurity standard meant to secure the Defense Industrial Base (DIB), a massive supply chain that handles both Federal Contract Information (FCI) and Controlled Unclassified Information (CUI).
Think of it like cyber driver’s licenses, you can’t take the wheel (a DoD contract) unless you’ve proven you can drive securely.
November 10 --> The Starting Gun...
On November 10, 2025, the DFARS amendment officially took effect, activating Phase 1 of CMMC 2.0 enforcement.
Phase 1 allows self-assessments for Level 1 and most Level 2 organizations, with results logged into the Supplier Performance Risk System (SPRS). Later phases (rolling out through 2028) will escalate requirements, meaning third-party and government audits will become the norm.
Translation... right now you can still self-report, but that window is closing fast.
What This Means for Contractors and Partners...
If you handle FCI or CUI, you’re in scope. Whether you’re building components, providing IT services, or managing data, you need to be CMMC compliant.
Prime contractors will push compliance down-chain. Expect major primes (Lockheed, Raytheon, etc.) to require subcontractors to show proof of compliance before signing on.
Non-compliance = non-eligibility. You won’t even be able to bid on certain DoD contracts without certification.
It’s not just red tape, it’s national security. The program was born from years of intellectual property theft and nation-state attacks on U.S. defense suppliers.
Some Common Pitfalls (and Pain Points I've witnessed)...
Thinking “we’re too small to matter.” Even small subcontractors handling CUI fall under CMMC. Attackers often target the “weakest link.”
Confusing “implemented” with “documented.” Having good security isn’t enough, you must prove it via an SSP (System Security Plan) and POA&M (Plan of Action & Milestones).
Underestimating the time needed. Realistically, closing NIST 800-171 gaps can take months. Waiting until a contract is on the table is a recipe for panic.
Believing self-assessment equals easy. DoD can audit your self-attestation. False claims can lead to False Claims Act penalties, a costly way to learn accountability.
CMMC --> More Than Compliance, It’s a Mindset Shift...
This isn’t just about checking boxes, it’s about institutionalizing security maturity. The DoD wants to ensure that every organization touching its data has a culture of cyber resilience, not just a policy binder collecting dust.
Think of CMMC as your fitness tracker for cybersecurity. It doesn’t make you fit, but it keeps you honest, accountable, and improving over time.
My Suggested CMMC 2.0 Readiness Checklist...
If your organization hasn’t started, here’s how to catch up fast.
Identify your required CMMC level. Determine if your contracts involve FCI, CUI, or both.
Perform a gap analysis. Compare your current controls to NIST 800-171 (for Level 2) and document gaps.
Build your SSP & POA&M. Write down how you meet each control and how you’ll fix the rest.
Implement missing controls. Prioritize multi-factor authentication, access control, encryption, logging, and incident response.
Assess and report. Submit your score to the SPRS and prepare for future third-party verification.
Maintain continuous compliance. Review, monitor, and update regularly, this is a journey, not a destination.
The Road Ahead...
CMMC 2.0 will roll out in phases through 2028. Over time, self-assessments will give way to independent audits, and the standard will evolve alongside frameworks like Zero Trust and AI-driven defense.
The DoD is serious about hardening its digital supply chain, and for once, the timing feels right. The threats have matured, the tools have improved, and now, so must the culture.
CMMC may have taken the scenic route to get here, but its arrival signals a new era of accountability and trust in the defense supply chain.
If you’re part of that ecosystem, don’t view this as another compliance burden, see it as your cybersecurity baseline for doing business in 2026 and beyond.
Because at the end of the day, cybersecurity isn’t just about compliance; it’s about credibility.
The IP HighWay
Stay updated with the latest IT security news.
info@iphwy.com
© 2025. IPHwy LLC. All rights reserved.



